Duo integrates with Microsoft Windows client and server operating systems to add two-factor authentication (2FA) to logins with a solution that balances security and usability. Access policies can be configured to block access to sensitive remote workstations from devices that are out of date or non-compliant with your security requirements.
For on-premises authentication, Active Directory is still king and Duo integrates seamlessly on Windows to protect unauthorized logins to console and RDP sessions. To do this, Duo has a Windows software client to install which provides secondary authentication to Duo after the initial authentication to Active Directory. Duo Authentication for Windows Logon and RDP Duo integrates with Microsoft Windows client and server operating systems to add two-factor authentication to Remote Desktop and local logons and credentialed UAC elevation prompts. The user may be seen as unenrolled if they are logging in with a username format that is not recognized by Duo. If users are logging in with more than one username format, make sure the Microsoft RDP application in your Duo Admin Panel is configured to normalize usernames. This document details the installation steps for the Duo Windows RDP (Remote Desktop Protocol) client. Install this to set up two-factor authentication using Duo for your Windows server. Request Duo Application Keys for Your Server. Each server should have its.
Duo integrates with Microsoft Windows client and server operating systems to add two-factor authentication to Remote Desktop and local logons and credentialed UAC elevation prompts. Duo Authentication for Windows Logon add Duo two-factor authentication to Windows desktop and server logins, both at the local console and incoming Remote Desktop (RDP) connections.
Today, I am going to how to step by step configure them.
Sig up Duo free account
1.Sign up a DUO trial account, it will support 10 users account with unlimited servers for free. Enter your information and click Start My Trial.
2.Duo will send a verification link to the email address for registration.
3.Login to the email account, open the welcome to Duo email, click Verify Your Email.
4.On the Step 1, enter the password and then click Continue.
5.On the Step 2, follow the introductions to install Duo Mobile on your phone and Add account via scan barcode.
6.You will see a green check mark on the barcode after you add account succeeded, click Continue.
7.On the Step 3, enter the Phone number, click Finish.
8.On the Setup Complete page, click Duo Push to Confirm Your Identity.
9.On the Setup Complete page, you will see sending on the Duo Push.
10.the sending Login request will pop up at the Duo Mobile app of your phone, click Approve.
11.Click Approve to allow you to access the Duo admin panel.
Edit Policy
1.On the Duo Admin Panel page, select Policies.
13.On the Policies page, click Edit Global Policy.
14.On the Edit Policy page, select New User Policy.
15.On the New User Policy page, select Deny access, click Save Policy.
Enroll a User
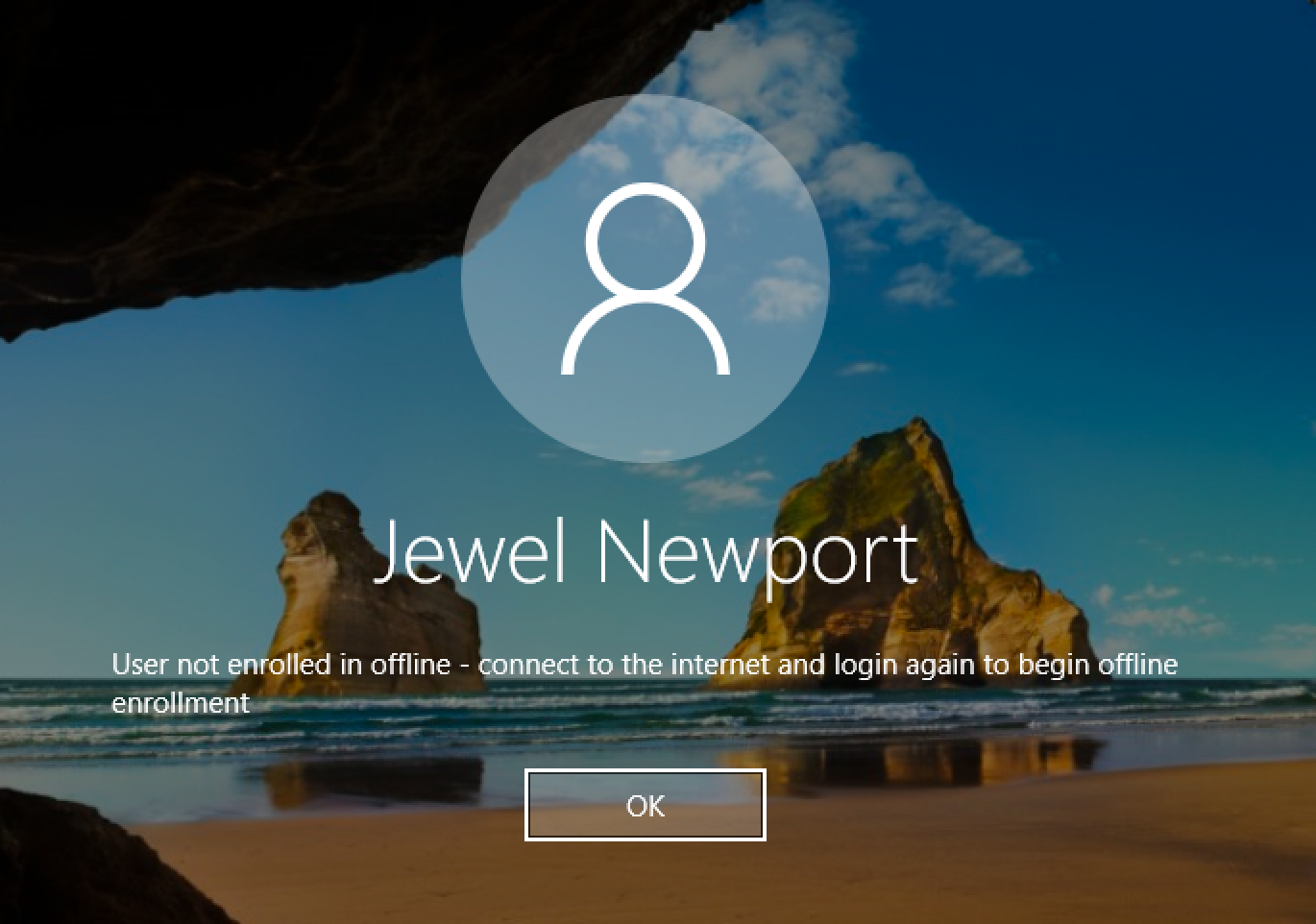
There are many ways to add users, I am going to add users manually. The username should match your Windows logon name. Install Duo Mobile and add your account to it so you can use Duo Push. If the user logging in to Windows after Duo is installed does not exist in Duo, the user may not be able to log in.
1.On the Duo Admin Panel, select Users.
2.On the Users page, Click Add User.
3.Type in the username. A Duo username should match the user’s primary authentication username. Duo usernames are not case-sensitive and are normalized to lowercase, click Add User.
Please don’t put the domain name in front of username. E.g. if the domain user account is carysun.comcsun, you need to put csun only. That means if there are the same username at multiple domains, you can use the same username for multiple domains login with 2FA authentication.
4.On the User page (in my case is csun), enter settings values, click Save Changes.
- Username: you can add username aliases by click Add username alias, if you have a different username at multiple domains, you can add them here but there are up to 4 aliases.
- Full name: Type in full name of the user
- Email: Type in email of the user.
5.Once the user is created you can click the Send Enrollment Email link to send the new user a message that contains a link they can use to add a phone or other 2FA authentication device.
6.Login to the email account from phone, open the Duo Security Enrollment email, click the link to enroll a phone.
Configuring Duo Authentication for Windows Logon and RDP
1.Log in to the Duo Admin Panel and select to Applications.
2.On the Applications page, click Protect an Application.
3.On the Protect an Application page, locate the entry for Microsoft RDP in the applications list, click Protect.
4.On the Microsoft RDP page, click Click to view at Secret key.
5.To get the integration key, secret key, and API hostname. You’ll need this information to complete your setup at Servers.
6.Login to Windows Servers.
7.Download the Duo Authentication for Windows Logon installer package
8.Run the Duo Authentication for Windows Logon installer with administrative privileges.
9.On the Welcome page, click Next.
10.On the Duo Connectivity page, enter the API Hostname from the Duo Admin Panel and click Next.
If the connectivity check fails, ensure that your Windows system can communicate with your Duo API hostname over HTTPS (port 443).
If you need to use an outbound HTTP proxy in order to contact Duo Security’s service, enable the Configure manual proxy for Duo traffic option and specify the proxy server’s hostname or IP address and port here.
11.Enter the integration key and secret key from the Duo Admin Panel and click Next.
12.On the integration options page, keep the default settings, click Next.
13.On the Configure the behavior for the Smart Card provider page, keep the default settings if you don’t plan to use smart cards on the system.
14.On the Configure User Elevation Protection page, keep the default settings if you don’t need to enable UAC elevation protection.
15.On the Ready to begin the installation page, click Install.
Hope you enjoy this post.
Cary Sun
Twitter: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Author: Cary Sun
Cary Sun is a Principal Consultant, He has a strong background specializing in datacenter and deployment solutions, and has spent over 20 years in the planning, design, and implementation of network technologies and Management and system integration.He hold CISCO CERTIFIED INTERNETWORK EXPERT (CCIE No.4531) from 1999.Cary is also a Microsoft Most Valuable Professional (MVP) and Cisco Champion, He is a published author with serveral titles, include blogs on Checkyourlogs.net, author for many books. Specialties: CCIE /CCNA / MCSE / MCITP / MCTS / MCSA / Solution Expert / CCA
Blog:
http://www.carysun.com http://www.checkyourlogs.net http://gooddealmart.com
Twitter:@SifuSun
Overview
Microsoft Windows RDP can allow an attacker to bypass the lock screen on remote sessions.
Description
In Windows a session can be locked, which presents the user with a screen that requires authentication to continue using the session. Session locking can happen over RDP in the same way that a local session can be locked. CWE-288: Authentication Bypass Using an Alternate Path or Channel (CVE-2019-9510)
At this point, an attacker can interrupt the network connectivity of the RDP client system. The RDP client software will automatically reconnect to the remote system once internet connectivity is restored. But because of this vulnerability, the reconnected RDP session is restored to a logged-in desktop rather than the login screen. This means that the remote system unlocks without requiring any credentials to be manually entered. Two-factor authentication systems that integrate with the Windows login screen, such as Duo Security MFA, may also bypassed using this mechanism. We suspect that other MFA solutions that leverage the Windows login screen are similarly affected. Any login banners enforced by an organization will also be bypassed. It is important to note that this vulnerability is with the Microsoft Windows lock screen's behavior when RDP is being used, and the vulnerability is present when no MFA solutions are installed. While MFA product vendors are affected by this vulnerability, the MFA software vendors are not necessarily at fault for relying on the Windows lock screen to behave as expected. Note that this vulnerability was originally described as requiring Network Level Authentication (NLA). We have since confirmed that this behavior is present whether or not NLA is enabled. Also, some combinations of RDP clients and Windows versions prior to Windows 10 1803 and Server 2019 may also demonstrate automatic session unlocking upon RDP reconnect. In such cases, neither MFA integrated with the login screen nor login banner displaying is bypassed in our testing. Although these cases are a different issue than VU#576688, the workarounds listed in this vulnerability note should still be applied to prevent these similar symptoms. |
Impact
By interrupting network connectivity of a system, an attacker with access to a system being used as a Windows RDP client can gain access to a connected remote system, regardless of whether or not the remote system was locked. |
Solution
The CERT/CC is currently unaware of a practical solution to this problem. Please consider the following workarounds. |
Disable RDP Automatic Reconnection on RDP servers |
Vendor Information
Note that vendors other than Microsoft listed as 'Affected' are simply indicators that the vendors have products that are affected by this vulnerability in Microsoft Windows RDP. The vendors' actual products do not necessarily contain a vulnerability, but rather that the vendor has a product that may not provide the login protection as expected, as the result of this issue with Microsoft Windows. |
Centrify Affected
Notified: June 05, 2019 Updated: June 06, 2019
Statement Date: June 06, 2019
Status
Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Duo Security Affected
Notified: April 22, 2019 Updated: June 18, 2019
Status
Affected
Vendor Statement
The Windows login/lock screens are secured by credential providers that collect credentials and perform other authentication-related activities, such as multi-factor authentication (MFA). Some are provided by Microsoft—the most common one being the password provider that usually collects the password as part of login. Other third-party providers, such as Duo, work similarly to the Microsoft providers, but add an additional element of MFA to the login.
With changes introduced in v1803 of Windows 10 and Server 2019, Microsoft has decided to use the credentials cached on the client machine to both re-authenticate the connection and unlock the previously-locked desktop, upon reconnecting Remote Desktop Protocol (RDP) sessions. In doing so, Microsoft has hindered credential providers from being able to prompt when a machine is unlocked in this context. By forcing the use of cached credentials, Microsoft has broken functionality used by credential providers to add resilience to this workflow.
To be clear, this is not a vulnerability or defect in Duo's service, but rather, it is a defect in how Microsoft has decided to unlock reconnected RDP sessions that have cached, valid authentication credentials without prompting the user.
We are unaware of Microsoft providing any effective workarounds for this unexpected change, but will continue to evaluate options to provide an integration as was previously achieved. We hope that Microsoft will provide appropriate configuration to allow those that want the previous functionality to be restored to be able to do so.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Vendor References
Microsoft Affected
Notified: April 19, 2019 Updated: June 11, 2019
Statement Date: May 29, 2019
Status
Affected
Vendor Statement
After investigating this scenario, Microsoft has determined that this scenario
is using valid, cached credentials. It does not compromise security boundaries
or bypass security features. Therefore it does not meet the Microsoft Security
Servicing Criteria for Windows. The RDP behavior change observed in VU#576688
was introduced in Windows Server 2019. The change allows the connection to
proceed in the earliest phase of connection. As long as it is connected, the
client will cache the credentials used for connecting and reuse them when it
needs to auto-reconnect.
As a best practice, Microsoft recommends that users always lock the client RDP
and all computers when unattended.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Okta Inc. Affected
Notified: June 05, 2019 Updated: June 07, 2019
Statement Date: June 06, 2019
Status
Affected
Vendor Statement
This is not a vulnerability or defect in Okta’s service or multi-factor
authentication (MFA) integration to Windows Server. Rather, this is an issue in
how Microsoft unlocks reconnected Remote Desktop Protocol (RDP) sessions
without calling the credential provider.
The Okta MFA Credential Provider does not currently support Windows 10 or
Windows Server 2019. However, any organization that has chosen to use the Okta
MFA Credential Provider for Windows 10 or Windows Server 2019 may be vulnerable
to this Microsoft issue, and users may not be prompted for authentication or
MFA upon re-establishing an RDP session.
As of June 6, we are unaware of any official Microsoft fix, and advise our
customers to reach out to Microsoft for next steps.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Vendor References
Authy Not Affected
Notified: June 05, 2019 Updated: June 06, 2019
Statement Date: June 05, 2019
Status
Not Affected
Vendor Statement
We do not provide windows login integration at any level.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Gemalto AV Not Affected
Notified: June 05, 2019 Updated: June 17, 2019
Statement Date: June 17, 2019
Status
Not Affected
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Silverfort Not Affected
Notified: June 05, 2019 Updated: June 17, 2019
Statement Date: June 05, 2019
Status
Not Affected
Vendor Statement
Due to the way our products operates, we are not affected by this vulnerability. We use a unique technology which allows us to enforce MFA on top of the authentication protocol itself (e.g. Kerberos, NTLM, LDAP) without relying on Windows login screen.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Vendor References
TUNIX Digital Security Not Affected
Updated: June 11, 2019
Status
Not Affected
Vendor Statement
TUNIX/Authenticationservice interacts at a level that is not affected.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
AuthLite Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Idaptive Unknown

Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
ManageEngine Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Ping Identity Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
RSA Security, Inc. Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Duo Rdp Windows
SecureAuth Unknown
Notified: June 05, 2019 Updated: June 06, 2019
Statement Date: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Symantec Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Vasco Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Duo Microsoft Rdp Login
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
Duo For Rdp
Watchguard Technologies, Inc. Unknown
Notified: June 05, 2019 Updated: June 05, 2019
Status
Unknown
Vendor Statement
We have not received a statement from the vendor.
Vendor Information
We are not aware of further vendor information regarding this vulnerability.
View all 17 vendors View less vendors
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 4.6 | AV:L/AC:L/Au:N/C:P/I:P/A:P |
| Temporal | 4.1 | E:POC/RL:U/RC:C |
| Environmental | 4.2 | CDP:ND/TD:H/CR:ND/IR:ND/AR:ND |
References
Acknowledgements
Thanks to Joe Tammariello of the SEI for reporting this vulnerability.
This document was written by Will Dormann.
Other Information
| CVE IDs: | CVE-2019-9510 |
| Date Public: | 2019-02-19 |
| Date First Published: | 2019-06-04 |
| Date Last Updated: | 2019-06-19 02:24 UTC |
| Document Revision: | 136 |
